Kevin thompson solarwinds ceo passport arrested, Solar Winds hq raided fbi
U.S. Treasury, Trade Depts Hacked Through SolarWinds Compromise
Communications in the United States A supply chain assault on SolarWinds, a security provider that allows the federal government and a number of Fortune 500 companies to track the health of their IT networks, allegedly compromised the Treasury and Trade Departments. In view of the large client base of the firm, experts suggest that the incident may be just the first such disclosure.
According to a story from Reuters, hackers in the United States have allegedly monitored internal email traffic in Russia. Departments of Treasury and Commerce. The attackers have unexpectedly abused SolarWindows' updates on their Orion site, a set of network management tools, reports Reuters.
Austin, Texas, recognized its systems in the security advisory to be "expertly sophisticated and manual suppliers on the Software Manufacturing of the SolarWinds Orion Platform, released from March 2020 to June 2020, for versions of 2019.4 HF 5 through 2020.2.1."
The Department of Cybersecurity and Infrastructure Security Agency (CISA) has undertaken an unprecedented action to issue a directive for emergencies to order the department of domestic security to withdraw the affected Orion goods from its networks immediately. In response to intrustions to the Treasury and Commerce Department.
"Treat all SolarWinds Orion monitoring software hosts as threat actors compromise and assume that additional continuing operation mechanisms have been deployed," advised CISA.
A Microsoft blog post says that the attackers have been able to apply malicious code to Orion's software updates. "This leads to a network base for the attacker to use to gain high levels of credentials," Microsoft wrote.
From there the attackers may build single sign-in tokens that impersonate the current users and accounts of the company, including highly privileged network accounts.
"The attackers may add their own credentials to the existing application service principals by using high-privileged accounts acquired using the above technique or by some other means so that they can call up APIs with authorization for the application," Microsoft explained.
Malicious code applied to the updating of the Orion program could have not been found on the host systems due in part to advice from SolarWinds itself, thanks to virus software and other security resources. SolarWinds says its products do not work properly in this support advisory except for antiviral scans and community policy object restrictions in its file directory.
The past of Reuters cites many unnamed sources that the trade and treasury intrusions may be just the tip of the iceberg. It looks like a fair bet.
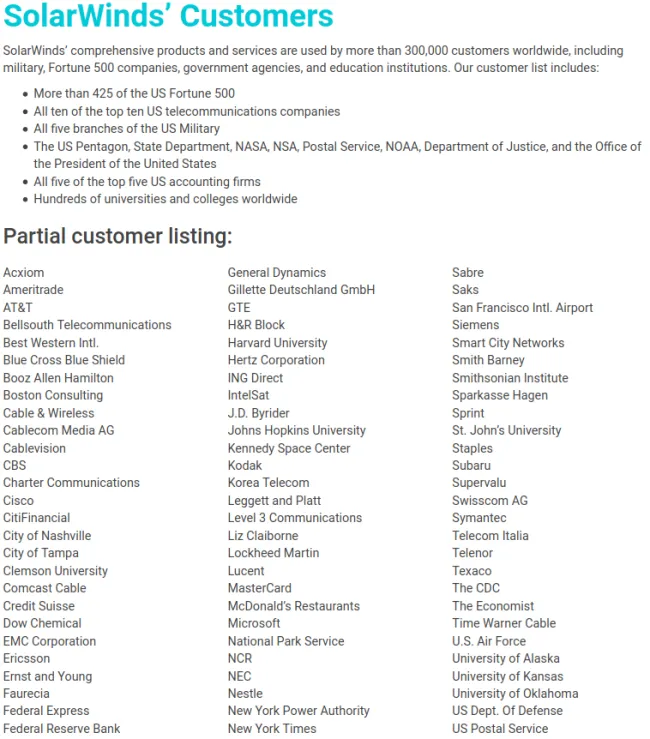
SolarWinds says that its clients include more than 300,000:
- more than 425 of the U.S. Fortune 500
- the Pentagon
- the State Department
- the National Security Agency
- the Department of Justice
- The White House.
How many of SolarWinds' customers are consumers of the goods of Orion impacted is not clear. However the supply chain attack by Reuters against SolarWinds is related to a large-scale campaign involving the recently exposed hack at FireEye in which hackers are able to access a wide range of proprietary devices used by the company to help consumers detect security problems on their computers and networks.
The breaches in the U.S. federal agencies have been expected to be made earlier this summer and hackers working for the Russian government are blamed.
In its very own advisory, FireEye announced that from March through May 2020, several updates contaminated by a malicious backdoor program have been digitally signed on the SolarWinds website.
FireEye has a widespread effect on SolarWinds, impacting public and private organisations.
"Victims have included North America, Europe, Asia and Middle East governments, consulting, technology, telecoms and mining," said the analysts. "In other countries and vertical areas we anticipate additional victims."
August 20:30 Update Update ET: In the previous version of this article, FireEye attributed the SolarWinds attack to APT29 incorrectly. The story has removed the detail.
